Flipper Zero Overview

what is a flipper zero?
Flipper Zero is a portable multi-tool for pentesters and hardware geeks in a toy-like body. It loves to explore the digital world around: radio protocols, access control systems, hardware, and more. The main idea behind the Flipper Zero is to combine all the research & penetration hardware tools that you could need on the go in a single case. Out of the box, Flipper is filled with features and skills, but also It’s open-source and customizable, so you can extend its functionality in whatever way you like, along with the community.
what’s inside a flipper?

what can it do?
From the above image we can see that the Flipper device is compact and has a couple of components like;
- A Sub 1 GHz antenna
The Flipper Zero can scan, capture and playback certain radio frequencies. It can mostly open devices like car key fobs, IoT sensors, garage doors, parking gates etc. Unfortunately, for most of the key fobs I tested used rolling codes which the Flipper can’t decrypt. To decrypt rolling codes you need another device like the HackRF with a PortaPack.
- GPIO Headers
Flipper Zero has a standard 2.54 mm GPIO header on the side, connected to the MCU pins. There are SPI, I2C, UART and other peripheral offered by our STM32. These pins can be used to connect 3rd party devices via industrial protocols. GPIO has 3.3V and 5V pins which allow to power connected module directly.
- IR LED & Receiver
The Flipper contains an infrared transceiver and it can help one control TVs, ACs, Audio Systems and other devices that use infrared signals. You can also save a specific remote signal and you can then turn your Flipper into a remote.
- RFID Board (which also reads NFC)
RFID is an increasingly common technology that allows for small amounts of data to be transmitted from a non-powered device, like an access card or a product tag, to a reader, such as a door lock or a register. The Flipper Zero can read RFID values, save, and replay them.
- USB HID Device Emulation
Flipper can be connected to your PC as a HID device, a flash card, or a COM port. If you’ve ever used a Bash Bunny you can use your Flipper as one. For those familiar with Ducky Script you can use the Flipper to perform “Bad USB” attacks. This means when you plug the Flipper in a computer you can select a script for the computer to run which can be malicious like collecting passwords or getting initial access or a prank like playing a Youtube video or displaying some text on screen.
unboxing
Since I wasn’t one of the original Kickstarter backers I waited for when they briefly opened up sales early June 2022.
I didn’t buy any additional items like the cover, screen protectors or a WiFi Dev Board. I only bought the Flipper and it cost as shown below;

The Flipper box contains a Flipper Zero, a USB-C cable, a quick start guide and a laptop sticker!
NB: It doesn’t ship with a SD card. You’ll need to buy one and I’ve found out that a 32GB one works perfectly!

how to use the flipper zero
To use the Flipper one has to update it using qFlipper to update the firmware. There are 3 major firmwares;
- Official Firmware – The official firmware that has frequency limitations based on the location you shipped the Flipper to.
- Unleashed Firmware – Based on the official firmware but Frequency-unlocked with rolling codes support & community plugins.
- RogueMaster Firmware – Based on the Unleashed firmware with assorted community plugins, tweaks & games.
Personally I use the unleashed firmware but if you’re a plugin junky then RogueMaster is a better fit for you.
NB: For a fresh firmware install you have to first flash with the official firmware before switching to Unleashed or RogueMaster.
This is to make sure that the databases and SD card are setup correctly.
Steps to install the Official firmware using qFlipper on Windows/Linux
- Download the program from the website Flipper Zero Update Page.
- Download the installation file for your operating system. (supported versions include Linux, Windows 10, 11).
- Run the installation file and follow the instructions from here.
what i’ve currently been able to do with the flipper
Since there’s only one Tesla in Kenya and I don’t know the owner I couldn’t open the electric charging port like the other cool kids, I decided to do other things with the Flipper.
I was able to emulate a friend’s parking card and paid for parking with my Flipper. The parking ticket uses a Mifare Classic 4K card. This is basically a contactless smart card that has RFID Read/Write capabilities. The Flipper can emulate the card very well as it reads all it’s individual segments, saves it and is later emulated at the parking station.
The MIFARE Classic cards have different applications like;
- Public transportation
- Electronic toll collection
- School and campus cards
- Internet cafes
- Access Management
- Car Parking
- Employee Cards
- Loyalty cards
How does one clone a card?
- Navigate to NFC on your Flipper
- Select Read and place your card on the back of the Flipper wait for it to read the entire card and save it for later.
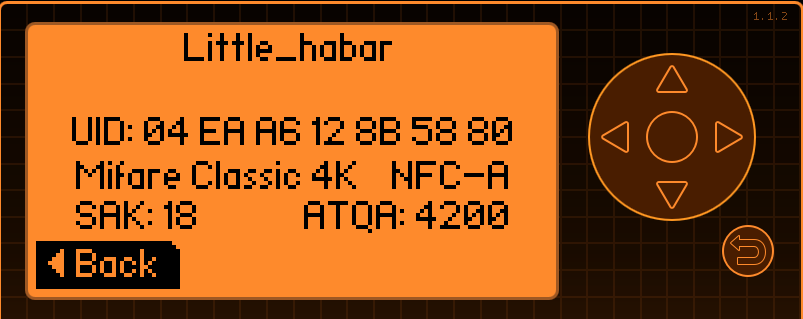
Now we have a card that we can emulate later. Below is a small GIF of me using my Flipper to pay for parking

Brief overview of MIFARE Classic 4K card vs MIFARE Classic 1K card
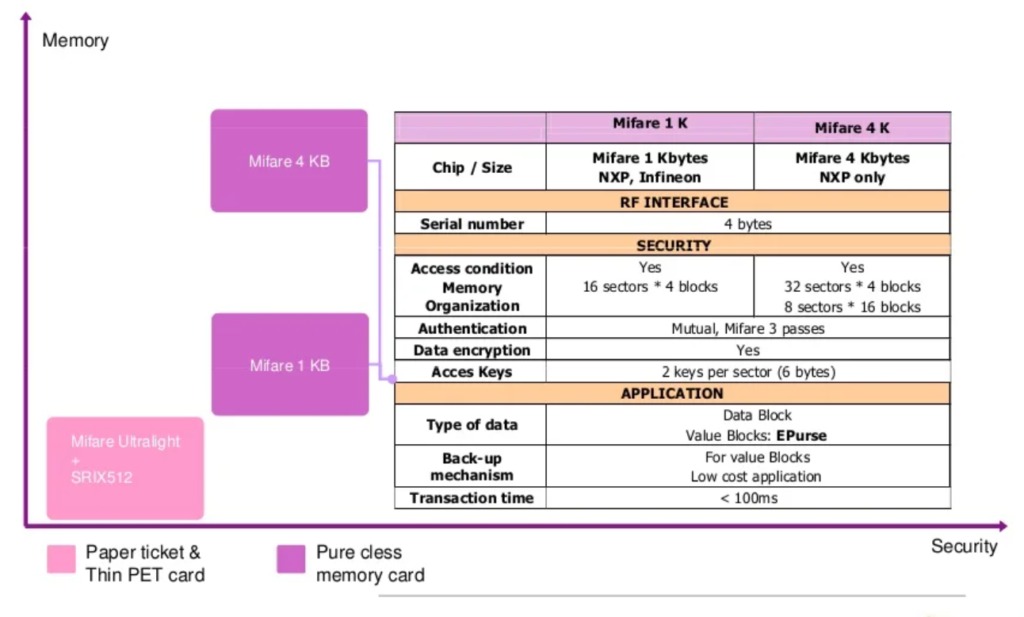
From the above screenshot obtained from https://www.slideshare.net/GlenCifuentesToro/mifare-cards , we can see the differences are mostly in memory organization and the chip sizes.
Weaknesses of MIFARE Classic
- Mifare cryptography is proprietary and has been broken because of the small key length (48 bits) and a badly designed algorithm.
- It is possible to make Mifare 1K and 4K clone cards as shown earlier.
- NXP Semiconductors (the manufacturers) have introduced a new generation of Mifare cards called MifarePlus that have better cryptography (AES-128) and ISO 14443-1 compliance.
Other things I was able to do;
- Use the Flipper as a U2F (Universal 2nd Factor) device. However, this isn’t a very valid use case for it after going through a very informative Twitter thread by Joe Fitz here that explains some good reasons not to use your Flipper as a U2F key.
- Play with BadUSB. I own a BashBunny so this wasn’t a new feature for me and there is a great community that shares very cool scripts for these attacks that i’ll share later as I compile the resources. NB: Before running any script please go through the code and understand what it does first!
- I’ve been able to switch off random TVs in restaurants because the Flipper has a universal TV remote. You can switch off, mute, play around with volume or channels.
- Operate an adult toy here
getting started with the flipper community
The main reason for this blog was to provide a personal overview of this amazing device as well as also combine all resources and communities that have been helpful as I tinkered with it.
Firstly, we purchase the device from https://shop.flipperzero.one/. Unfortunately, they don’t ship directly to Kenya so you’ll have to use a shipping company for this.
The device is now in your possession, what next? We need to join the Flipper Zero community in Discord, Reddit and Telegram.
Helpful Communities and Resources
Official Discord Server – https://discord.gg/YYXwTqSsB2
Unofficial Discord Server – https://discord.gg/tjBxJJpw6p
Rogue Flippers Discord Server – https://discord.gg/MR3T9u6nRc – Mostly for RogueMaster firmware users
Flipper Zero Software Community Discord Server – https://discord.gg/Pu78Uh6J9m – For tinkerers who want to build their own firmware
Subreddit – https://www.reddit.com/r/flipperzero/
Flipper Zero Forum – https://forum.flipperzero.one/
Official Telegram – https://t.me/flipperzero
Unofficial Telegram – https://t.me/flipperzero_unofficial
Github Repositories
Awesome Flipper (A massive collection of awesome resources that is regularly updated) – https://github.com/djsime1/awesome-flipperzero – This is the best starting point for a newbie.
https://github.com/Eng1n33r/flipperzero-firmware/releases – Unleashed Firmware (unlocked)
https://github.com/sasiplavnik/Flipper-IRDB – An Extensive IRDB for the Flipper
https://github.com/logickworkshop/Flipper-IRDB – An Extensive IRDB for the Flipper
https://github.com/UberGuidoZ/Flipper – A great repository by one of the most active guys in the community!
http://flipper.pingywon.com/ – For anyone who likes the RogueMaster firmware.
https://github.com/nwhistler/flipper-tools – For MacOS BadUSB payloads
Documentation
The Flipper Team have great documentation for installation basics as well as the Flipper modules located at https://docs.flipperzero.one/
They also have a great blog that goes into details of the whole production process as well as some of the challenges they faced trying to obtain a certificate of compliance for their Sub-1 GHz design.
If you’re a tinkerer there is a great repo by atmanos on how to build your own firmware, plugins and debugging – https://flipper.atmanos.com/docs/overview/intro
what’s next
- Clone and emulate hotel key cards.
- Play with the WiFi Dev board once I get a hold of one.
- Play with multiple key fobs that don’t have rolling code support. The key fobs I was testing support rolling codes so I wasn’t able to perform a relay attack.
- In future, build my own firmware and plugins.
- Play with IoT devices like sensors, LEDs etc
- CyberPunk stuff like this
closing remarks
This is such a fun device to play around with (ethically of course). It has really made me very interested in RF and SDR hacking and will save up to buy the Hack-RF with a PortaPack.
I like how fast the community is growing and this can only mean that the device will only get better when more people get their hands on it and contribute to the community!
In Kenya, our Communications Authority has guidelines to be followed so if and when you get one and want to operate here you need to operate in the Citizen Band shown below;

resources
- https://github.com/djsime1/awesome-flipperzero
- https://github.com/UberGuidoZ/Flipper
- https://www.reddit.com/r/flipperzero
- https://docs.flipperzero.one/
- https://blog.flipperzero.one/
- https://docs.flipperzero.one/sub-ghz/frequencies
- https://www.ca.go.ke/wp-content/uploads/2018/04/Procedure-for-Licensing-use-of-Radio-Frequencies.pdf
- https://www.slideshare.net/GlenCifuentesToro/mifare-cards
donations
If this was helpful you can donate below so that I can buy that Hack-RF with a PortaPack
BTC: bc1qwnsyyr5ttg7ktfqcmxgfe3sjelhy79z3r6cp4j
ETH: 0xB927fa9E84bd8BA9b06A8615b600D1AFC13d4824
XMR: 46CGeEhuDnqciAvV6BgptGg1d8XeKSV5hMfoPR6z5vsj9H1wZmEjqyBR2QiQXusY8USsmYb1LchrQEsTvuuBUC9YCnAmbi3

0 Comments